Background
Malware bad actors just keep on coding and developing new threats with the stupid dream to get rich soon in their stupid heads. It's a serious moral corruption generated by whatever background they are raised, but that's a fact that is going on out there. Here is the case of those fact, but this one is escalated into quite harmful in threat level.. if released.. this will be more headache for researchers, industry and LEA (law enforcement agencies), so after internal meeting we decided to disclose it.
I suggest you pay attention for this disclosure. This post is a pure intelligence matter, we provided in comprehensive fact as evidence of crime, following by many of screenshots (with dates and some with URL) for your checking and comparison purpose.
As per previously post also mentioned, we (read: MalwareMustDie,NPO - Anti CyberCrime & Malware Research Group) work not only in defensive way but being active to spot the threat as early stage as possible, and inviting thus support law enforcement & CERT folks to initiate the crime case upon it.
Message to the Law Enforcement fellow is, all presented evidence in this post can be confirmed and checked by your side too, please don't let this malware spotted in the wild since judging by the current materials, boosted by some interest from the crooks that communicating each other in the bad bad forums, serious damage will be occurred for sure.
The idea to verdict of coding malware and an attempt to sell it (by himself) as business scheme (see the panels part) is already a serious crime that can be used as a base to act.
@INTERPOL_Cyber @Europol_EU @jaapvoss @CERTGIB @FBIMostWanted Please see this post & grab everything http://t.co/SHf6znirVj #MalwareMUSTDie
— MalwareMustDie, NPO (@MalwareMustDie) January 4, 2014The promotion of Prison Locker
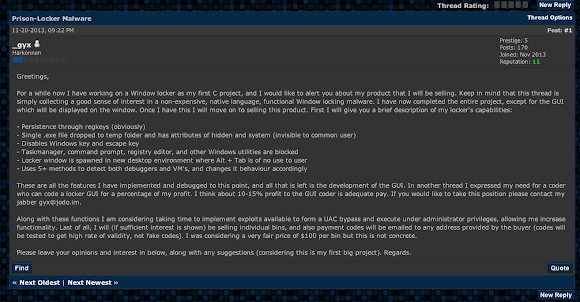
Started from the hacker forums we spotted the release attempt messages below:
Following by the next message:
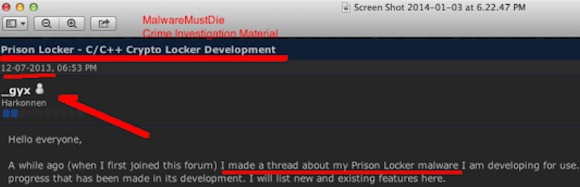
The better snapshot is below:
Finally the public attraction in paste bin (click to link to the paste):

This is where the name of Power Locker emerged.
The text of the "release note(? whatever they call it)" is interesting:
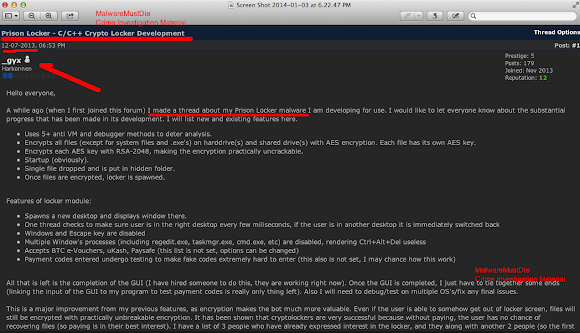
Hello everyone, A while ago (when I first joined this forum) I made a thread about my Prison Locker malware I am developing for use. I would like to let everyone know about the substantial progress that has been made in its development. I will list new and existing features here. Uses 5+ anti VM and debugger methods to deter analysis. Encrypts all files (except for system files and .exe s) on hard drive(s) and shared drive(s) with AES encryption. Each file has its own AES key. Encrypts each AES key with RSA-2048, making the encryption practically uncrackable. Startup (obviously). Single file dropped and is put in hidden folder. Once files are encrypted, locker is spawned. Features of locker module: Spawns a new desktop and displays window there. One thread checks to make sure user is in the right desktop every few miliseconds, if the user is in another desktop it is immediately switched back Windows and Escape key are disabled Multiple Window s processes (including regedit.exe, taskmgr.exe, cmd.exe, etc) are disabled, rendering Ctrl+Alt+Del useless Accepts BTC e-Vouchers, uKash, Paysafe (this list is not set, options can be changed) Payment codes entered undergo testing to make fake codes extremely hard to enter (this also is not set, I may chance how this work) All that is left is the completion of the GUI (I have hired someone to do this, they are working right now). Once the GUI is completed, I just have to tie together some ends (linking the input of the GUI to my program to test payment codes is really only thing left). Also I will need to debug/test on multiple OS s/fix any final issues. This is a major improvement from my previous features, as encryption makes the bot much more valuable. Even if the user is able to somehow get out of locker screen, files will still be encrypted with practically unbreakable encryption. It has been shown that cryptolockers are very successful because without paying, the user has no chance of recovering files (so paying is in their best interest). I have a list of 3 people who have already expressed interest in the locker, and they along with another 2 people (so the first 5, of which 3 are already filled) will receive a bin at a discounted price of $50. The regular price will be $100. If you would like to express interest in buying, please either PM me or contact my jabber: gyx@jodo.im . Messaging me on Jabber will get a response much quicker (I have other forums to pay attention to than HF obviously). I will update this thread with developments in the future. S/O to betamonkey who I respect very much.And has good responses from fellow crooks :-)
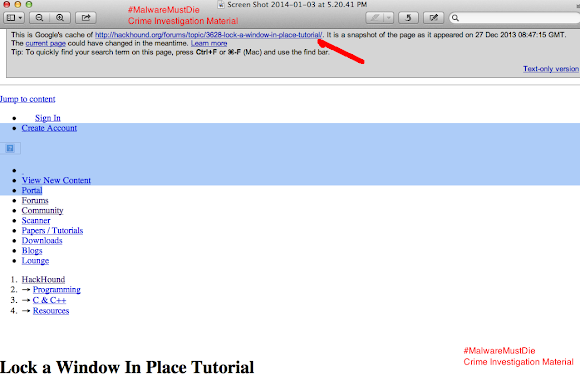
And in another forum also started some post of tutorials/manual:
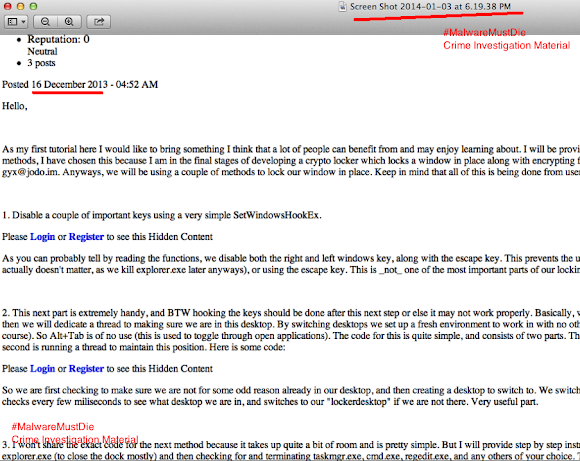
For all good people's conveniences, the text grabbed:
URL: h00p://hackhound.org/forums/topic/3628-lock-a-window-in-place-tutorial/ Lock a Window In Place Tutorial Started By gyx , Dec 16 2013 04:52 AM gyx Newbie Members Reputation: 0 Neutral 3 posts Posted 16 December 2013 - 04:52 AM Hello, As my first tutorial here I would like to bring something I think that a lot of people can benefit from and may enjoy learning about. I will be providing a tutorial on how to lock a window in place using some basic methods, I have chosen this because I am in the final stages of developing a crypto locker which locks a window in place along with encrypting files. If you are interested in buying message me on jabber: gyx@jodo.im. Anyways, we will be using a couple of methods to lock our window in place. Keep in mind that all of this is being done from userland. 1. Disable a couple of important keys using a very simple SetWindowsHookEx. Please Login or Register to see this Hidden Content As you can probably tell by reading the functions, we disable both the right and left windows key, along with the escape key. This prevents the user from pressing the windows key to bring up the start menu (this actually doesnt matter, as we kill explorer.exe later anyways), or using the escape key. This is _not_ one of the most important parts of our locking code. 2. This next part is extremely handy, and BTW hooking the keys should be done after this next step or else it may not work properly. Basically, we will be creating a new desktop using the API CreateDesktop and then we will dedicate a thread to making sure we are in this desktop. By switching desktops we set up a fresh environment to work in with no other processes (other than those that Windows is always running of course). So Alt+Tab is of no use (this is used to toggle through open applications). The code for this is quite simple, and consists of two parts. The first is putting us in the right desktop if we are not there, and the second is running a thread to maintain this position. Here is some code: Please Login or Register to see this Hidden Content So we are first checking to make sure we are not for some odd reason already in our desktop, and then creating a desktop to switch to. We switch to it, and then start our thread to stay there. The thread simply checks every few miliseconds to see what desktop we are in, and switches to our "lockerdesktop" if we are not there. Very useful part. 3. I wont share the exact code for the next method because it takes up quite a bit of room and is pretty simple. But I will provide step by step instructions on what needs to be done. Basically we will be closing explorer.exe (to close the dock mostly) and then checking for and terminating taskmgr.exe, cmd.exe, regedit.exe, and any others of your choice. The function that will be a thread should: Close explorer.exe using the command "taskkill /IM explorer.exe /F" using whatever API of your choice to execute a Windows command. Enter a while(1) loop with maybe a Sleep(15) at the beginning. The loop should do the following over and over: Enumerate all processes open (this is computationally heavy thats why I recommend a Sleep(15)), google how to do this if you dont know how ;) Get the name of each process by using a simple for loop after opening the process (you should find some code if you google, hint: GetModuleBaseName for getting the process name). Compare the name to your list of applications to kill (strcmp(), it returns 0 if they are identical), and execute the following command if they are identical: "taskkill /IM processname.exe /F". You cant close a Windows process such as taskmgr using a normal API call or even a normal taskkill /IM call, the easiest way to do this (that I have found) is using the taskkill command with /F (force) on there. You can again use whatever method for executing a Windows command that you choose, I use WinExec with the SW_HIDE parameter to prevent a cmd prompt from being displayed. One thing I have noticed about this part is that you may need to play with the number of and locations of Sleep() commands, or else a bunch of cmd prompts may pop up over and over. Personal hint: split this up into two functions, one the enumerate all procs and one to get the name and terminate if it is on the list. So in review, the sequence of steps for our basic locking mechanism should be: Switch desktops and maintain our position there. Lock the keys. Kill explorer and moniter for our list of "bad" processes, kill them if they exist. Create our window to display, it should be fullscreen (you can find how to do this with a quick google). This can go anywhere after switching desktops really, doesnt matter too much. Well thats all I plan to put in this tutorial as I dont want to give out all my methods or spoonfeed you. But I hope you enjoy this and learned a little something. :) Back to top
And then also some Q & A comment from the coder:
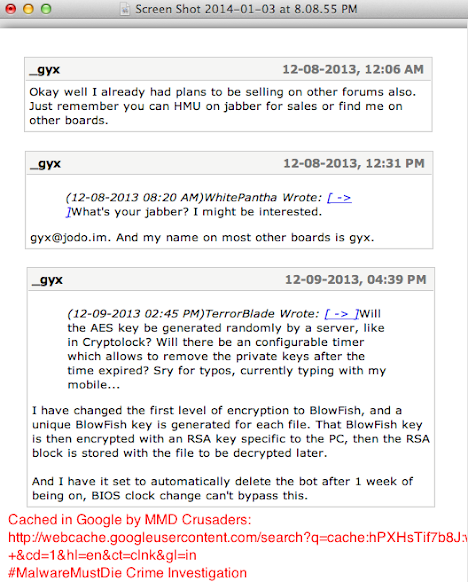
Another one:
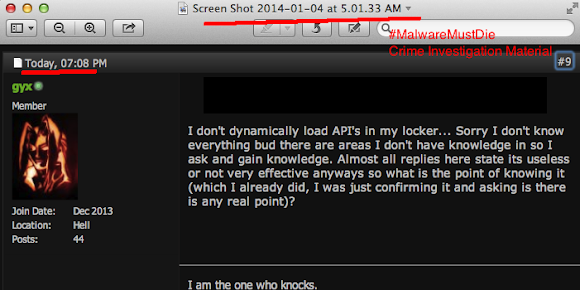 Oh BTW please don't tell us that this guy is innocent..
Oh BTW please don't tell us that this guy is innocent..
Full dox info of #MalwareMustDie Crusader & Prison Locker coder is shared 24H for #evidence http://t.co/SHf6znirVj pic.twitter.com/RlrqzgT74O
— MalwareMustDie, NPO (@MalwareMustDie) January 4, 2014God bless the braves, thank you crusader!
Another attempt/vector for "other" threat post back then was also detected by the same bad actor:

Well, it looks like he was investigating some flaw in browser too < to be noted by internet browser's vendors.
The identification
The ID is obvious. Which all are lead you to the bad actor's ID below: (picture?)
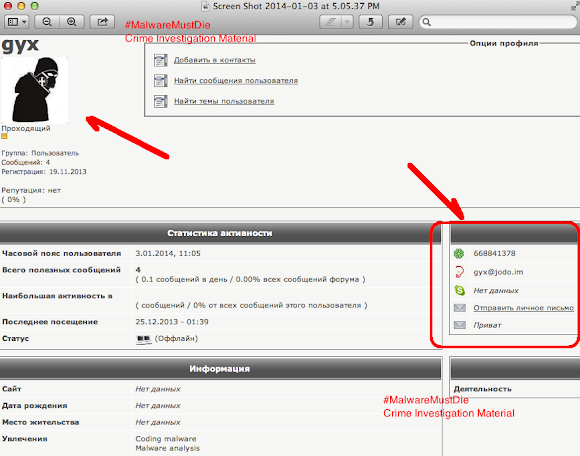
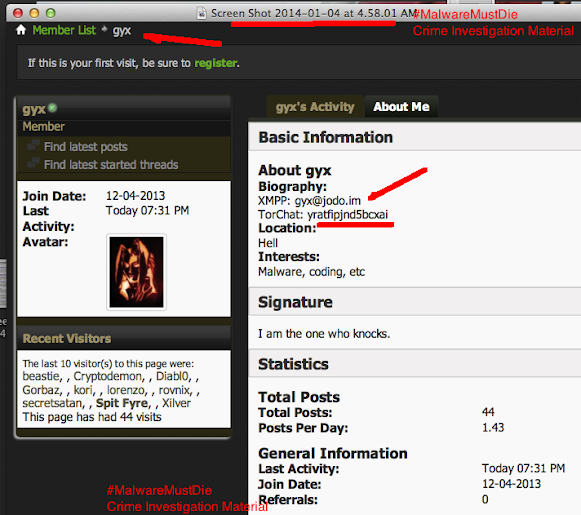
It wasn't that hard to confirm the bad actor's (the malware coder's) ID, our team filled Google with its cache now (hope is enough) for the PoC:
Like this..)

..and this:
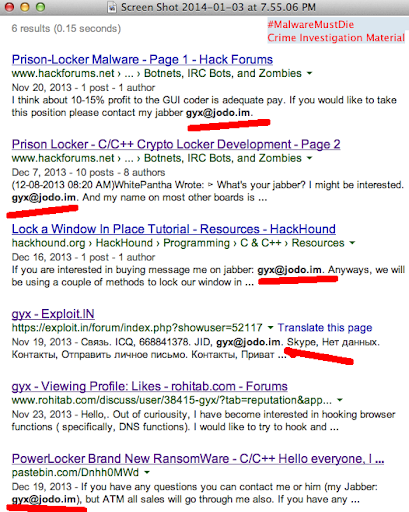
A bit shocky part is, "our suspect" was pretending (or) to be a researcher, see the ICQ number of the blog below for the comparison: Tweet Analysis shows: This is the panels screenshot promoted by the bad actor himself,
Obviously our crusader also spotted same threat too, I should notice this sooner :-)
@MalwareMustDie Looks same guy, https://t.co/UJvZLK2gXM #PowerLocker #ransomware #MMD! @MalwareMustDie pic.twitter.com/xapsVjpKki @Grimdotnet @Grimdotnet checked. I miss posted for the twitter account. thats our guy. ICQ matched. Or he must explain why it matched. All of the materials involved by this threat ail be shared offline to our partners & friends via secure vetted interface. Updates and mass investigation level is going to be released in our forum. Some data will be changed upon investigation progress.
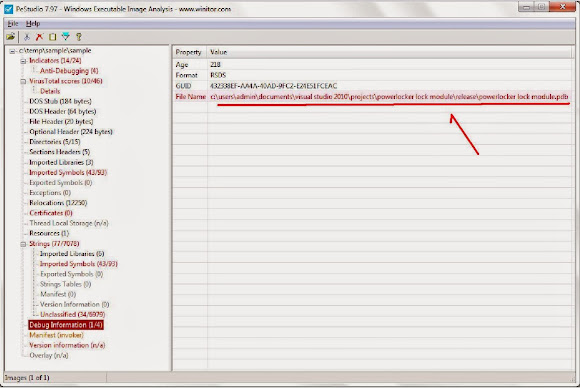
1. We still monitor the case's progress and they realized that we extract the correct information. We also found that the plan to sell the malware (upon released) is still on schedule. Furthermore, the "marketer" actor of this malware product was responding to this blog disclosure as per pasted below: 2. The closest information to the identification of the bad actor via public access is: 3. The marketer "Prophyry" (lives in Michigan, US) burped a doubtful information: For the clarification of some dilemma that may occurred we added this section; Since there is a progress in public that may doubt the dangerous facts of the threat, we are releasing the static binary analysis of sample 17FB3E3B3FD3CA7FB9E5F59BBF2CF234 mentioned above. I used to analyze the sample in almost every cases posted in this blog, but in this case, to make the pure objectivity of the analysis result, I invited the expert of static binary analysis, the author of Windows PE binary analysis tool "PeStudio", Mr. Marc Ochsenmeier from Germany, to investigate the binary with the static analysis. as per below details.
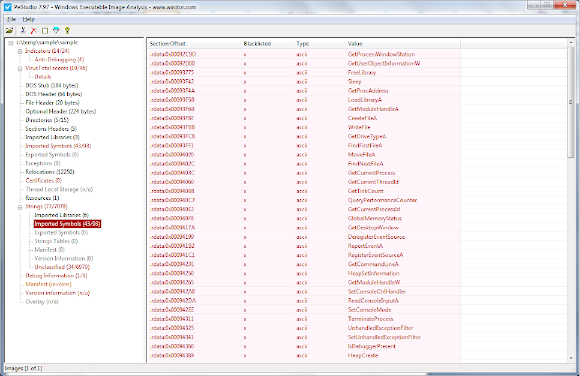
The binary was statically analyzed, with the method as per quoted below: Below are several screenshots of PeStudio tools GUI describing the malicious points explained in the report made by Marc, and if I may comment, PeStudio is a very useful tool (most of MalwareMustDie members are supporting the development and using it) to perform Windows PE static binary analysis, that can breakdown the details of the binary details to be easily reviewed and learned. A tool that I can recommend for malware research, here is the access-->>[HERE]
Malicious Sign Indicators: By seeing thee above static analysis you maybe can tell whether the "sample" of PowerLocker is actually exist or not. The malware was not distributed widely because many of good people gather with us and making effort to interfere and disturb the bad actor's work, these gentlemen were actually spending their private time, taking many risk by doing hard work confronting the bad people while most of us were in New Year's holiday and celebrating.
PandaLabs Blog is just releasing a nice analysis of the threat in their blog here-->[PandaLabs] We really hope that the coder and the marketer individuals who are supporting this malware's development can be stopped by law enforcement by an arrest, since we worry that they are still eager to release it as per planned.
Stay safe, friends. MalwareMustDie!

Can you figure which account he is owning in twitter? :-) the #w00tw00t attack is the clue :D
Following, the account he owned (twitter):

This person has a lot to explain and look forward to hear it.

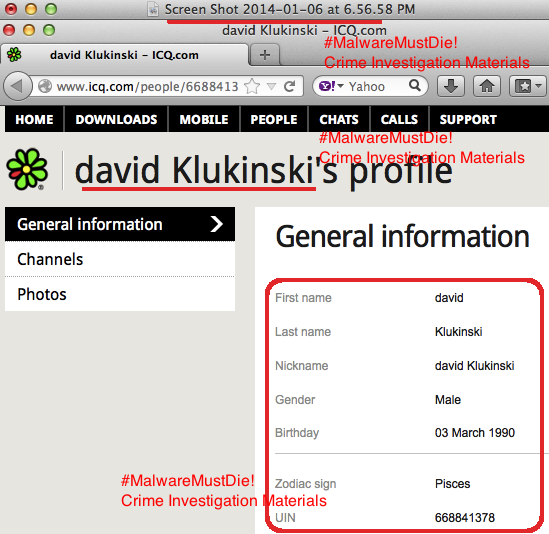
OK, we leave it to the law enforcement to do the rest, but I suggest you all mark this IDs, friends. And I don't believe in coincidence. Additionally in the bottom of this post there is the ID of ICQ Account available-->>[LINK]
Commercial aspect of the malware - The panels
these were two nice panels to be nuked down :-)


Pardon for the correction
The shares
(NEW) Recent Updates Information

We urge law enforcement to start the investigation and all of the materials posted in this blog is formed to be used as crime evidence.

4. Clarification & Static Analysis of Sample 17FB3E3B3FD3CA7FB9E5F59BBF2CF234
A clarification
We were not releasing information of the any sample or source codes we secured since there was no infection in the wild that can be described as the activity of malware infection, and there was NO RELEASE / FINAL version spotted at the time this blog's post was first written. What we spotted was the development effort and result of the software project that was designed to perform malicious ransom action by actors described in the above section in this post in details. As for the evidence we managed to secure some, and one of the sample was spotted in December 2013, with the hash of 17FB3E3B3FD3CA7FB9E5F59BBF2CF234, found & reported by our group's supporter during the surveillance session of this threat, further information can not be exposed due to the nature of security, intelligence and supporting to the work of our friends in law enforcement.
Our disclosure is to draw attention of the law to make swift action accordingly in order the disrupt the bad actor's plan to release the product in time.
Static Analysis
The goal of PeStudio is to detect anomalies, suspicious hints and other particularities of Windows Portable Executables and provide "Indicators" about the level of trust one can have about the image analyzed. The ultimate goal of PeStudio is to give a true/false about if an image is malware or not.
The complete process is static. The image is never started. No attempt of any dynamic and/or runtime decryptor is made. No Reverse Engineering or code analysis is done.
Report of Marc's static binary analysis in the PDF can be viewed here -->>[Report in PDF]
Report Snapshot: (small size only)


Additional Analysis
Thank you very much for the link to our post! Greets to friends in Panda Labs for a good post: @Luis_Corrons @Panda_Security